Boolseeker
Introduction
Lately, I have been diving into numerous mobile penetration testing assessments. Every time, the first hurdle is the same—getting past those pesky security hardening mechanisms. To simplify this process, I created Boolseeker.
Boolseeker is a straightforward yet powerful tool designed to quickly analyze APK files and identify crucial but simply implemented security mechanisms using boolean logic.Specifically, it searches for mechanisms related to:
- Rooted Device Detection: Identifies whether the device has been rooted, which can compromise its security by allowing unauthorized access to the system.
- Emulator Detection: Detects whether the app is running in an emulator, which can be used for reverse engineering or testing in a controlled environment.
- Runtime Integrity Verification: Ensures that the app’s code and memory have not been tampered with during runtime, protecting against runtime attacks.
- File Integrity Checks: Verifies that critical files and configurations have not been altered, helping to ensure the app's integrity and security.
Boolseeker extracts all boolean Java methods along with their full paths, saving them to an output file. It also hunts for specific keywords within these methods and can even search for them in native shared object (SO) files.
In mobile penetration testing, bypassing these hardening checks is often one of the initial tasks. From my experience with various mobile penetration testing projects, it’s clear that the first step is typically to circumvent these checks. Surprisingly, many banking apps still rely on straightforward checking methods with functions that return boolean values.
The main goal of Boolseeker is to save time by automating the search for these checks in android applications, eliminating the need to manually sift through them using decompiling tools like jadx-gui.
Installation
Visit official GitHub repository: https://github.com/0xdeny/boolseeker
1. Go Installation
Ensure that Go programming language is installed on the system by following the official installation guide available here.
2. Apktool Installation
For debian based systems like Kali Linux make sure apktool is installed:
sudo apt install apktool3. Boolseeker Installation
Get started by installing Boolseeker:
go install github.com/0xdeny/boolseeker@latestUsage
The primary function of Boolseeker is to extract all boolean Java method names with their full paths and save them to an output text file. It also searches these methods for keywords related to detection and defense mechanisms.
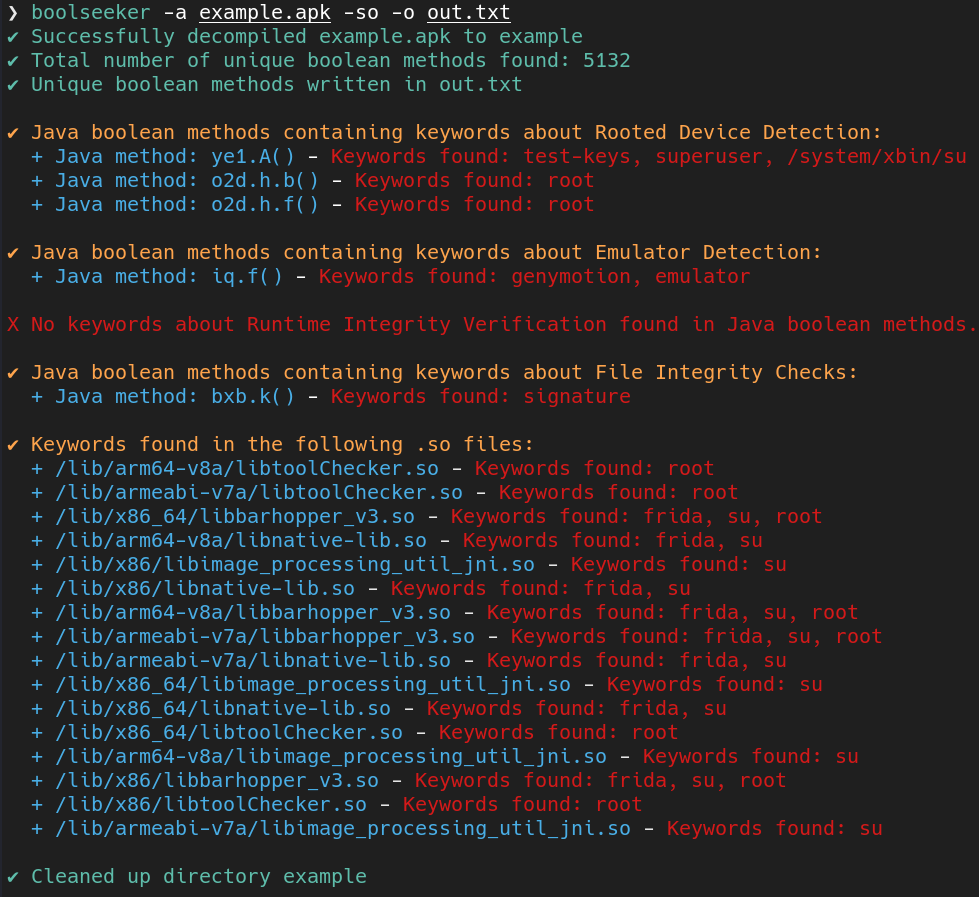
Additionally, Boolseeker offers the option to scan shared object (SO) files for keywords, helping to identify potential detection mechanisms within the native C functions of the Android application.
Here are some screenshots to give a better idea of how the tool works:
- Main function of Boolseeker:
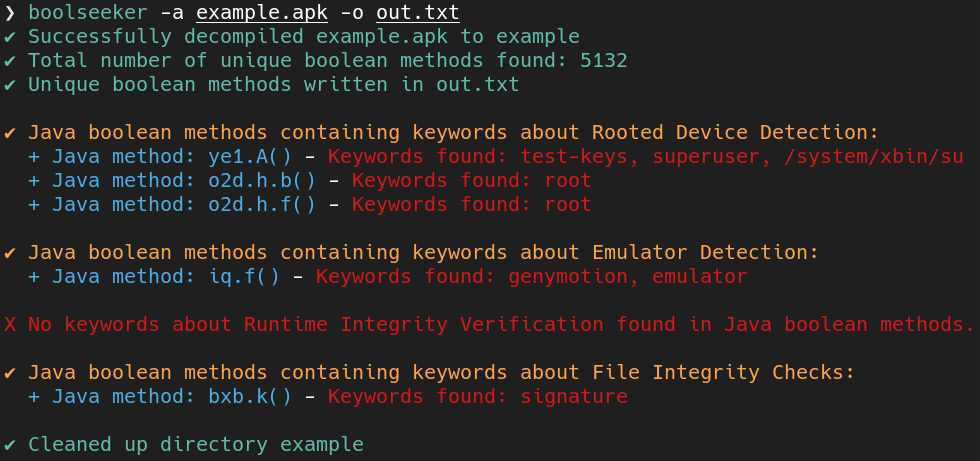
- Main function of Boolseeker plus additional scan in shared object (SO) files:
Add New Keywords
New keywords can also be added to search for in Java methods and Native C functions.
For Java methods:
- Start by adding all the keywords to search for to the
keywordsslice, regardless of their association with any specific detection type:
func SearchKeywordsInMethod(methodContent string) ([]string, bool) {
keywords := []string{"ro.hardware", "ro.kernel.qemu", "ro.product.device", "ro.build.product", "ro.product.model", "ro.build.fingerprint", "/sys/qemu_trace", "/dev/qemu_trace", "/dev/socket/qemud", "/dev/qemu_pipe", "/system/bin/netcfg", "/proc/cpuinfo", "/proc/tty/drivers", "magisk", "root", "test-keys", "superuser", "Superuser", "daemonsu", "99SuperSUDaemon", ".has_su_daemon", "genymotion", "emulator", "nox", "27042", "frida", "27043", "FridaGadget", "xposed", "MessageDigest", "getPackageInfo", "signature", "/system/app/Superuser.apk", "/system/xbin/su"}
...- After including the keywords in the keywords slice in step 1, ensure that they are appropriately categorized in the corresponding slices in the main function. This organization allows Boolseeker to correctly identify and present the detection mechanisms associated with each category.
root_detection_keywords := []string{"magisk", "root", "test-keys", "superuser", "Superuser", "daemonsu", "99SuperSUDaemon", ".has_su_daemon", "/system/app/Superuser.apk", "/system/xbin/su"}
emulator_detection_keywords := []string{"ro.hardware", "ro.kernel.qemu", "ro.product.device", "ro.build.product", "ro.product.model", "ro.build.fingerprint", "genymotion", "geny", "emulator", "nox", "/proc/tty/drivers", "/sys/qemu_trace", "/dev/qemu_trace", "/dev/socket/qemud", "/dev/qemu_pipe", "/system/bin/netcfg", "/proc/cpuinfo", "/proc/tty/drivers"}
runtime_integrity_verification_keywords := []string{"27042", "frida", "27043", "FridaGadget", "xposed"}
file_integrity_keywords := []string{"MessageDigest", "getPackageInfo", "signature"}
...
For Native C functions:
- Add all the keywords to search for to the so_keywords slice. This should include keywords related to any of the four detection types. By doing so, the keywords can be checked in the native C functions as well. This approach ensures that if the application cannot be made to function normally (as if the device were legitimate) after bypassing Java method functions, potential detection mechanisms in the shared object (SO) files can still be identified.
if *searchSo {
so_keywords := []string{"frida", "xposed", "su", "root", "magisk", "/sbin/su", "test-keys"}
...Conslusion
Boolseeker is designed to streamline the process of identifying security hardening mechanisms in mobile applications, whether they're implemented in Java methods or native C functions. By automating the search for critical boolean logic checks and specific keywords, Boolseeker helps penetration testers efficiently uncover potential vulnerabilities and bypasses. This tool ultimately saves valuable time and effort, making mobile security assessments more effective and less cumbersome.